Identifying Our Target
To find a client that we can attack (legally) to practice reconnaissance, we use the public bugbounty program bugcrowd.com.
There are programs on their website that allow you to attack their websites or part of their websites, report bugs to the website owner and receive a payment as a reward.
TESLA was used as an example in “Practical Ethical Hacking”, but one definitely has to make sure that the program is still active before one starts any hacktivity against some website. On the bugcrowd website, click on “Products” to see all active bugbounty programs. TESLA can be found with the search bar on top of the page.
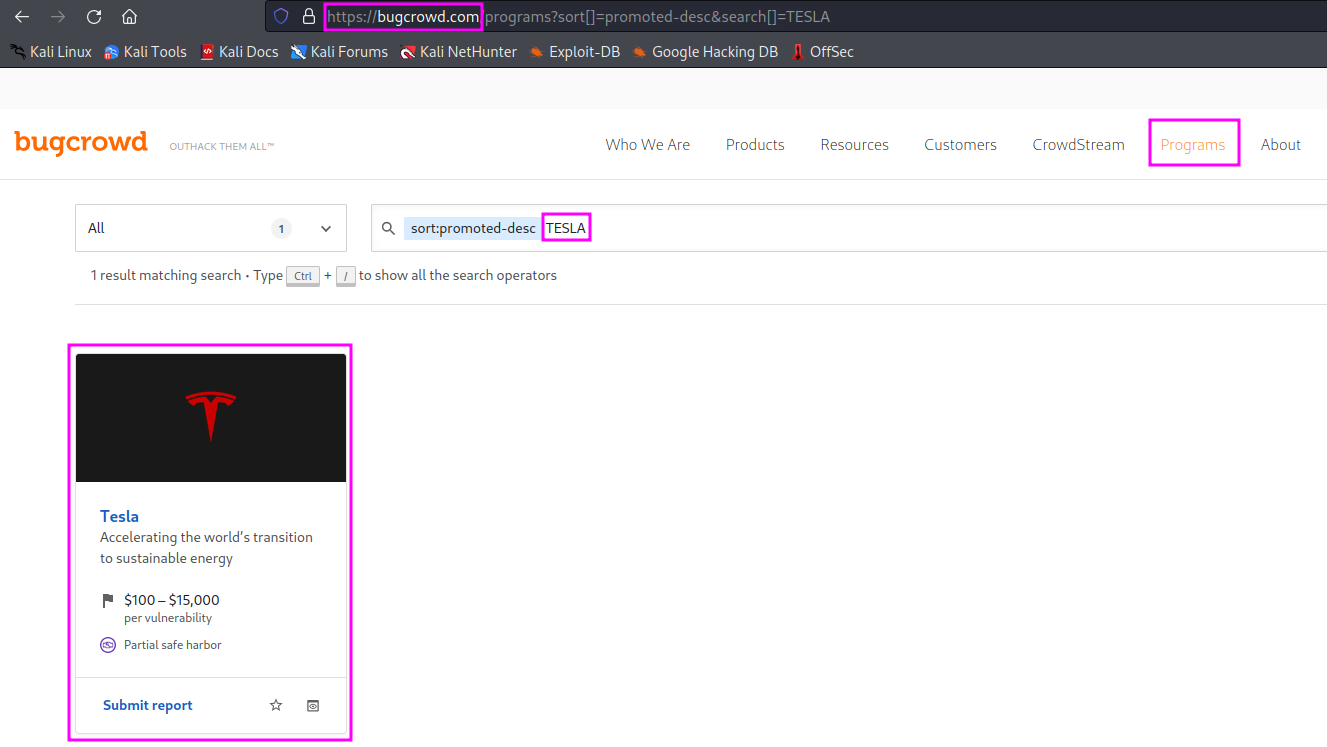
One should read the “Rules of Engagement” thoroughly, especially the websites that are out of scope.